Introduction to Cyber Security
Message from the Writer
MCQ Type Basic Idea
-
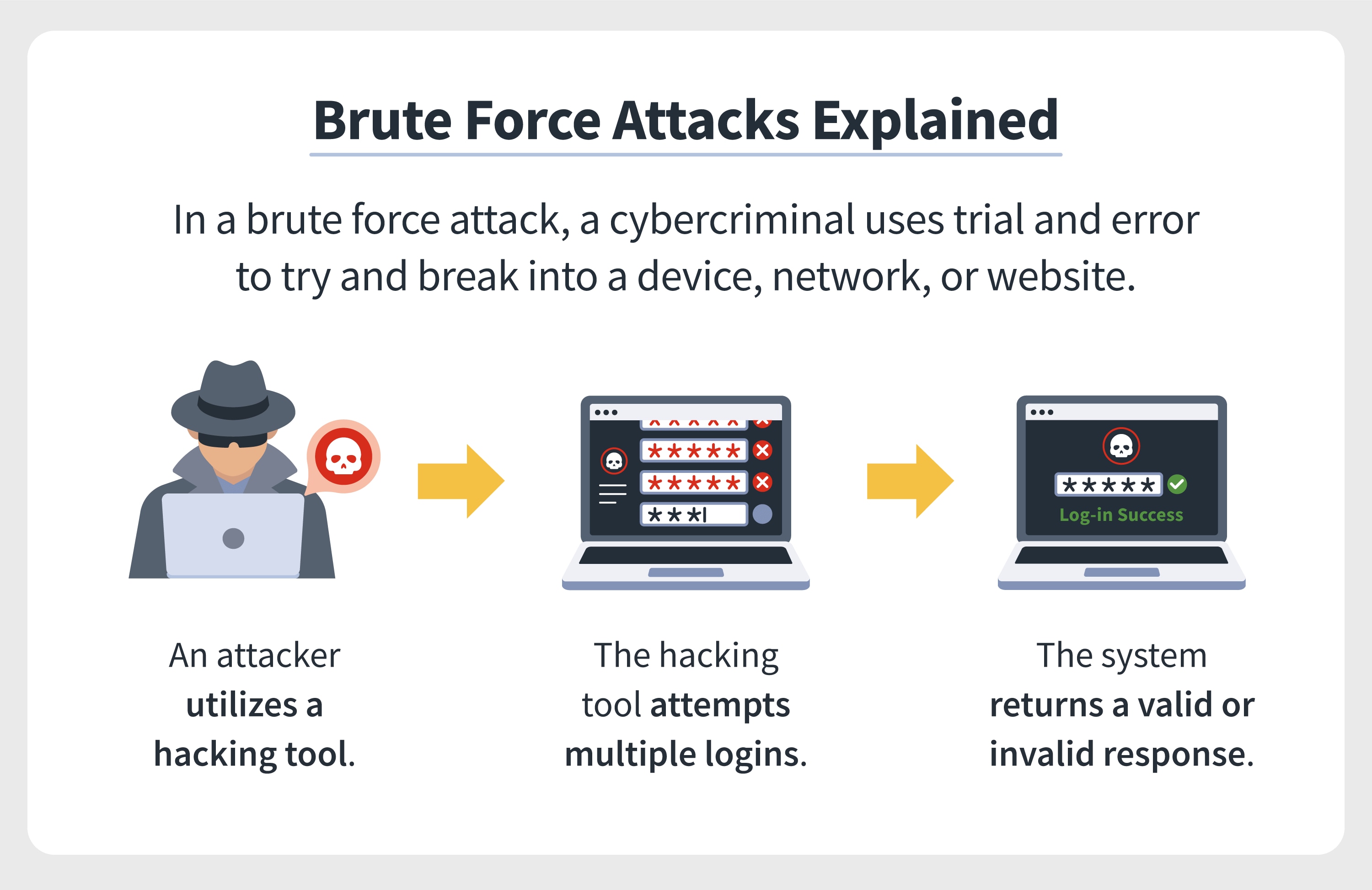
Programs that multiply like viruses but spread from computer to computer are called as.
a) Worms
b) Virus
d) None Of these
c) Boot
Answer
a) Worms
-
Which Of the following is a cybercrime?
a) Hacking
b) Cyber bulling
d) All of these
c) Virus attack
Answer
d) All of these
- DLL stands for
a) Dynamic Link Library
c) Link Library
b) Digital Link Library
d) Domain Link Library
Answer
a) Dynamic Link Library
- Hackers who release information to the public is
a) a black hat
b) a grey hat
c) a white hat
d) a brown hat
Answer
b) a grey hat
- Which Of the following is a social Engineering site?
a) ebay
b) facebook
C) amazon
d) CWB
Answer
a) ebay
- Validation Of the source Of information is known as
a) Confidential
b) Authentication
c) Non-repudiation
d) Data integrity
Answer
b) Authentication
- The Dos attack is one type of
a) Active Attack
c) Brute force attack
b) Passive Attack
d) None of these
Answer
a) Active Attack
- Traffic analysis is one type of
a) active attack
c) brute force attack
b) passive attack
d) none of these
Answer
b) passive attack
- Chain & Abel is a popular .
a) password cracking
c) security
b) networking
d) messenger
Answer
a) password cracking
- Hacktivism is
a) Activism
c) Passive hacking
b) Hacking for a cause
d) Malicious hacking
Answer
b) Hacking for a cause
- Banner grabbing is an example of what?
a) Passive operating system fingerprinting
b) Active operating system fingerprinting
c) Footprinting
d) Application analysis
Answer
a) Passive operating system fingerprinting
- What is the full form of CERT/CC?
a) Computer Engineering Response Team Co-ordination Centre
b) Computer Emergency Record Team Co-ordination Centre
c) Computer Emergency Response Team Co-ordination Centre
d) Computer Engineering Record Team Co-ordination Centre
Answer
c) Computer Emergency Response Team Co-ordination Centre
- LDAP stands for
a) Lightweight Directory Access protocol
b) Lightweight Data Access Protocol
c) Lightweight Domain Access Protocol
d) Lightweight DNS Access protocol
Answer
a) Lightweight Directory Access protocol
- What is enumeration?
a) Identifying active systems on the network
b) Cracking passwords
c) Identifying users and machine names
d) Identifying routers and firewalls
Answer
(c) Identifying users and machine names
Start With Introduction
Conventional & Cyber crime
a) Brief comparison between a conventional crime and a cyber crime. b) List the motives and reasons behind cyber crimes.
Answer
a) Crime is a social and economic phenomenon and is as old as the human society. Crime is a legal concept and has the sanction of the law. Crime or an offence is "a legal wrong that can be followed by criminal proceedings which may result into punishment." Cyber-crime is the latest and perhaps the most complicated problem in the cyber world. "Cyber crime may be said to be those crime, where either the computer is an object or subject of the conduct constituting crime. "Any criminal activity that uses a computer either as an instrumentality, target or a means for perpetuating further crimes comes within the ambit of cyber crime."There is apparently no distinction between cyber and conventional crime. However on a deep introspection we may say that there exists a fine linc of demarcation between the conventional and cyber crime. The demarcation lies in the involvement of the medium in cases of cyber crime. The prerequisite for cyber crime is that there should be an involvement of the virtual cyber medium at any stage.
b) The crimes and criminals in the cyber world vary little from their physical world counterparts. Historically, and today, the same laws are used to prosecute both (ie: trespass, fraud, theft, copyright violation). The motives and profiles of criminals in the virtual world are as varied as in the physical world. Motives include financial benefit, thrill seeking, revenge, knowledge, and beliefs. Where the two worlds begin to diverge is in the lingo being built for the criminal using the computer in his crimes. A script kiddie is someone with a low technical skill level and ofa young age. A hacktivist seeks to further his views by promoting them or striking out at those who hold opposing views. A web defacer targets websites that can be penetrated and changed. Crackers circumvent copy protection mechanisms. Pirates make or distribute unauthorized copies of protected programs or works. Lamers have a low technical skill level and largely reuse the work of others. Phreakers target telephone systems. The term hacker is primarily used to describe those who participate in the insightful or intuitive exploration of systems. These activities are, in of themselves, benign but the term has also become linked with the cyber criminal. The term cracker is generally reserved for hackers with criminal intentions. Hackers often align themselves in groups. They exchange details of their exploits on web sites and through Internet Relay Chat (IRC) messages. They contribute technical knowledge to their group and even participate in collaborative attacks.
Strong,Weak,Random Password
Define strong, weak and random password with examples.
Answer
A password that is difficult to detect by both humans and computer programs, effectively protecting data from unauthorized access. A strong password consists of at least six characters (and the more characters, the stronger the password) that are a combination of letters, numbers and symbols (@, #, $, %, etc.) if allowed. Passwords are typically case- sensitive, so a strong password contains letters in both uppercase and lowercase. Weak passwords refer to any passwords that can be easily guessed, either because it's so personal to a person or because it hardly takes any time to find it via the brute-force method, where a hacker (here, a hacker being anyone who's intent on finding your password, be they a criminal in Belarus or your nosey kids) runs through all possible password options. A random password generator is software program or hardware device that takes input from a random or pseudo-random number generator and automatically generates a password. Random passwords can be generated manually, using simple sources of randomness such as dice or coins, or they can be generated using a computer.
Computer Virus and Worm
Write down the difference between computer virus and worm
Answer
A computer virus attaches itself to a program or file enabling it to spread from one computer to another, leaving infections as it travels. Like a human virus, a computer virus can range in severity: some may cause only mildly annoying effects while others can damage your hardware, software or files. Almost all viruses are attached to an executable file, which means the virus may exist on your computer but it actually cannot infect your computer unless you run or open the malicious program. A worm is similar to a virus by design and is considered to be a sub-class of a virus. Worms spread from computer to computer, but unlike a virus, it has the capability to travel without any human action. A worm takes advantage of file or information tranSport features on your system, which is what allows it to travel unaided.
Software Piracy
What is software piracy? Discuss about the preventive measures against software piracy.
Answer
1st Part: Software piracy is the stealing of legally protected software. Under copyright law, software piracy occurs when copyright protected software is copied, distributed, modified or sold. Software piracy is considered direct copyright infringement when it denies copyright holders due compensation for use of their creative works.
2nd Part: Here are some of the tips to prevent or lessen software piracy: Code Key - For the past 5 to 7 years, software developers have devised a plan to lessen or prevent software piracy. This is by using a code key. A code key comes with the software that we buy. Before fully installing the software on our computer, we must provide the specific code key that came with the software. After providing the code key, we can run the software on our computer. The code key also locks after it has been used. This is so that the software cannot be installed on other computers after it has been installed on one. We will have to call the manufacturer of the software to be able to use the code key again. This is not good news to people who pirate software.
Open Source - Open source software is described as a free software that anyone can download from the Internet. A lot of different software can are licensed as open source. Open source software are under the license free software license. There are also different upgrades for these open source software that can also be freely downloaded from the Internet. By using open source software, people don't need to worry about spending a lot of money for original copies of software. This will also lessen the number of people who are using pirated software as there are alternative programs that can be used and they do not have to pay fines when they are caught.
Hardware Key - A hardware key is a device that is used for anti-piracy. This tool prevents software vendors to distribute their products or use them without authorization from the copyright owner of the software. The hardware key works when it is attached to a computer. It monitors software licensing and enforces licensing of the protected software those are detected on the computer. This tool will lessen software vendors from illegally distributing the software that they have and is a good prevention measure for piracy.
Anti-Piracy Software - There are different types of anti-piracy software that are available for free. Anti-piracy software is used to prevent illegal duplication or illegal use of copyrighted software. There is also an anti-piracy software that prevents hackers from getting into the software and copying it without consent from the copyright owner. Some of them are also already integrated on the disks of the software that contains the program. This may also be for piracy music. The anti-piracy association is also looking for other ways to prevent software piracy. Reporting anti-piracy may prevent it from happening.
Hackers, Crackers & Phreakers.
Explain the difference between Hackers, Crackers and Phreakers.
Answer
A hacker is a person intensely interested in the arcane and recondite workings of any computer operating system. Hackers are most often programmers. As such, hackers obtain advanced knowledge of operating systems and programming languages. They might discover holes within systems and the reasons for such holes. Hackers constantly seek further knowledge, freely share what they have discovered, and never intentionally damage data.
A cracker is one who breaks into or otherwise violates the system integrity of remote machines with malicious intent. Having gained unauthorized access, crackers destroy vital data, deny legitimate users service, or cause problems for their targets. Crackers can easily be identified because their actions are malicious.
Phreaks (or phreakers) are usually motivated more by technical curiosity and the hacker ethos than any criminal intent (although phreaking is most certainly illegal). To bounce a call through a dozen different switching systems around the world, to our friend next door - all for free - is regarded by phreaks as an accomplishment. The fact that they are committing fraud and felonies in the process is regarded as incidental - or perhaps part of the fun.
For Easy Understanding, you can read the below article.
| Hacker | Cracker |
|---|---|
| The good people who hack for knowledge purposes. | The evil person who breaks into a system for benefits. |
| They are skilled and have a advance knowledge of computers OS and programming languages. | They may or may not be skilled, some of crackers just knows a few tricks to steal data. |
| They work in an organisation to help protecting there data and giving them expertise on internet security. | These are the person from which hackers protect organisations . |
| Hackers share the knowledge and never damages the data. | If they found any loop hole they just delete the data or damages the data. |
| Hackers are the ethical professionals. | Crackers are unethical and want to benefit themselves from illegal tasks. |
| Hackers program or hacks to check the integrity and vulnerability strength of a network. | Crackers do not make new tools but use someone else tools for there cause and harm the network. |
| Hackers have legal certificates with them e.g CEH certificates. | Crackers may or may not have certificates, as there motive is to stay anonymous. |
| They are known as White hats or saviors. | They are known as Black hats or evildoers. |
- He is the one who is curious about workings of any computer software.
- Very often they are no other than unit of smart programmers.
- They have advanced knowledge of operating system and programming language.
- They require data concerned with variety of security holes, so they can exploit and damage or steal knowledge.
- They are the ones who break into different systems with malicious intent.
- They carry out activities like making unauthorized access, destroying necessary information, stopping services provided by server, etc.
- Crackers can easily be identified because their actions are malicious.
Phreakers
- They are the ones who gain illegal access to the telephone system.
- They are considered to be the original computer hackers as they are the ones who break into telephone system illegally and make long distance calls.
- Phreaker word is a combination of, “Phone” + “Freak”.
- Earlier, Phreakers whistled or used an instrument to mimic tones of phone system operators to route calls and identify payments to avoid paying for an expensive call. Thus, they basically attack phone systems to obtain free phone access or using the phone line to transmit viruses and access, steal and destroy data
- Now, they break into company’s system and manipulate data.
Cybercriminals plan attack
How do cybercriminals plan attack?
Answer
Cyber Criminals use many tools and methods to locate vulnerability of their victim. Following are three major phases involved in planning of cyber crime:
1. Reconnaissance: "Reconnaissance" means an act of reconnoitring. In this phase attacker try to explore and gain every possible information about target. They use active and passive attacks to get this information.
2. Scanning and Scrutinizing: In this phase attacker collects validity of information as well as finds out existing vulnerabilities. It is the key phase before actual attack happens.
- Port scanning: Identify all ports and services (open / closed)
- Network scanning: Verify IP address and network information before cyber attacks.
- Vulnerability scanning: Checking loop hole in system.
3. Launching an attack: Using the information gathered in the previous step, they attack the target system to gain confidential information about individuals or organizations. The attack is launched using the following steps:
- Crack the password.
- Exploit the privilege
- Execute malicious command
- Hide the files
- Cover the track.
LDAP and RAS security
Explain LDAP and RAS security for mobile devices. Discuss the implication for mobile devices.
Answer
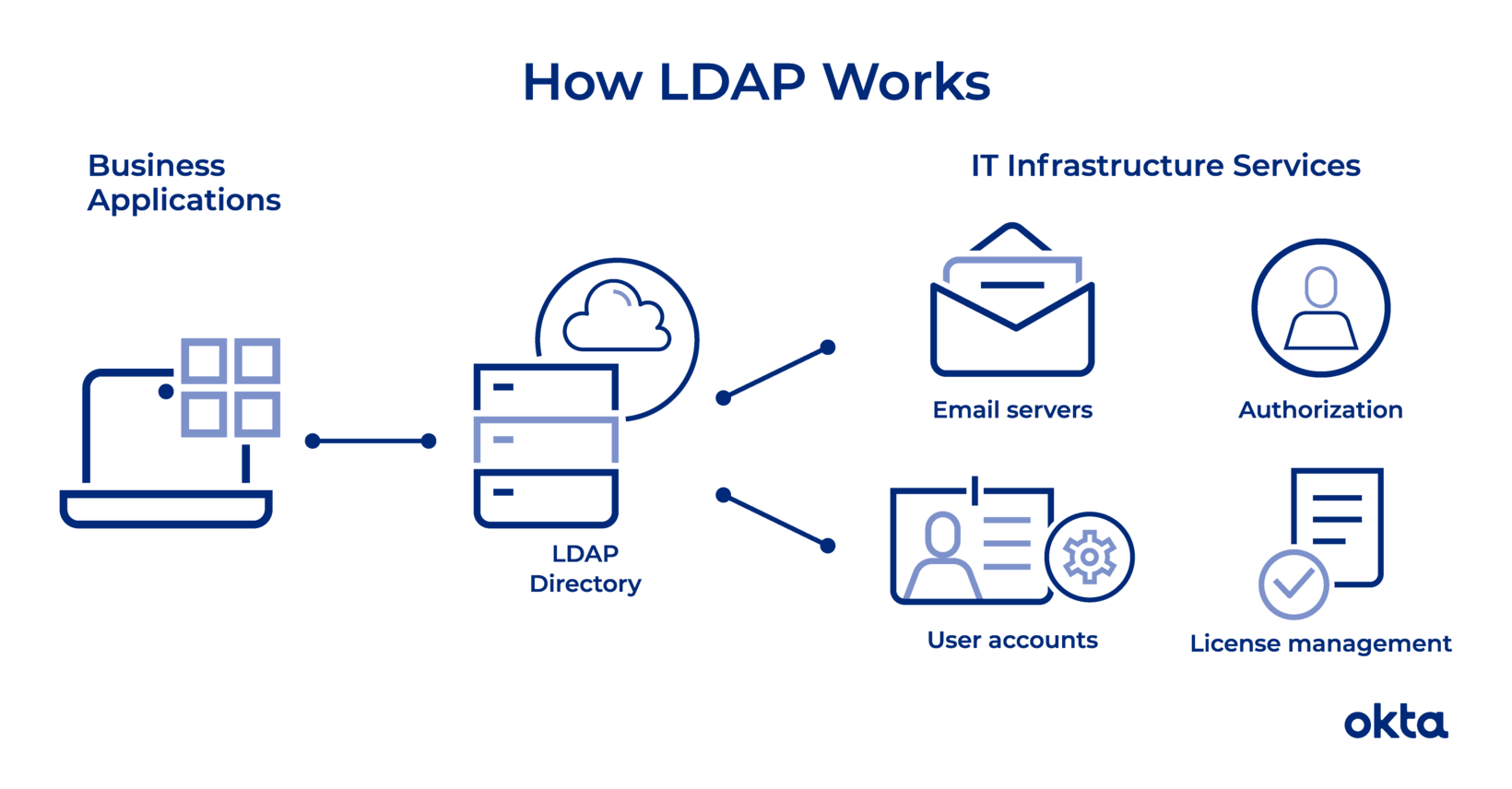
1St part: LDAP: The Lightweight Directory Access Protocol is one of the core protocols that was developed for directory services. LDAP is used to distribute lists of information organized into directory information trees, which are stored within a LDAP database. However, in order to access information stored within an LDAP database, the user must first authenticate their identity. It can deliver LDAP authentication as a cloud based service.
It is a software protocol for enabling anyone to locate organizations, individuals and other resources such as files and devices in a network, whether on the public internet. It is a lightweight version of Directory Access Protocol which is part of X.500, a standard for directory services in a network.
RAS security for mobile devices:
RAS provides security features to be ensure that corporate data remains secure even available over the wide area network. In mobile devices;
- It can robust the system.
- Protecting corporation data and guarding the network against threats.
- Highly definable permissions.
For Easy Understanding, you can read the below article.
Ras
- RAS(Remote Access Server) is a type of server that provides services to remotely connected users over a network or the Internet
- This software is designed to provide authentication, connectivity and resource access services to connecting users.
- Once connected with a RAS, a user can access his or her data, desktop, application, print and/or other supported services.
LDAP
- LDAP is a protocol that allows you to access and manage information stored in a directory.
- LDAP (Lightweight Directory Access Protocol) is one of the core protocols that was developed for directory services (the process of securely managing users and their access rights to IT resources)
Forgery Explain
What do you mean by the term forgery? Explain with example.
Answer
Forgery includes imitation of original paper or online documents for the intent to harm reputation, or cheat, individual or a group by means of telecommunication network is forgery. It includes fraudulent transaction of credit cards, postage stamps, seals, currency, immigration documents, signatures, bank checks, academic credentials, digital signatures on electronic documents, even medicines. Example: In year 2008, a cyber crime originated in UK, named as DarkMarket used to sell credit card, login information's to members who used to commit financial crimes and fraudulent transactions.
Maximum penalty for forgery
What is the maximum penalty for forgery?
Answer
If caught under the act of forgery, defined under Indian Penal Code section 463, 464 an offender will be punished with imprisonment from three to five years or will be charged with a fine upto 2 lakhs or both.
Classifications of hackers
What are the classifications of hackers?
Answer
Hackers are categorized into three kinds as black hat or crackers, white hat or ethical hackers, and grey hackers. Black hat hackers are normally crackers. They tamper website contents, forward spams, flood the network, and impersonate accounts. They always have malicious intent. White hat persons are ethical hackers who is responsible for finding the loopholes of a system. Industries employ white hats to find security cracks in the system or they are also employed if any attack has taken place. Study reports revealed that most of the industrial attacks are from inside. Someone who knows the security system very well and uses this skill to pose a threat to the organization can be called as grey hat. They behave ethical sometimes and crackers at other times.
Store passwords for System
What are the files that store passwords for Windows and Linux?
Answer
Windows stores encrypted files in SAM file under system32 while Linux stores passwords in /etc/shadow file.
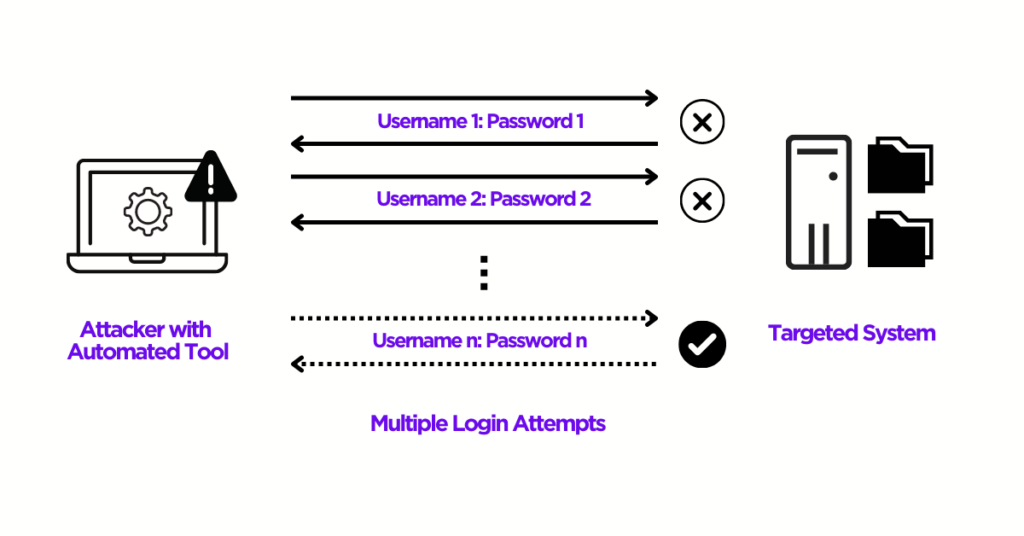
Password hacking methods
What are the different types of password hacking method?
Answer
There are two different categories for password hacking one is active and another is passive. Passive attack includes sniffing, masquerading, eavesdropping or playing man in the middle attack, dictionary attack, brute force attack. Active attack can include guessing, shoulder surfing, or social engineering.
For Easy Understanding, you can read the below article.
Passive attack
- Sniffing - In its simplest form, sniffing is the act of intercepting and monitoring traffic on a network.
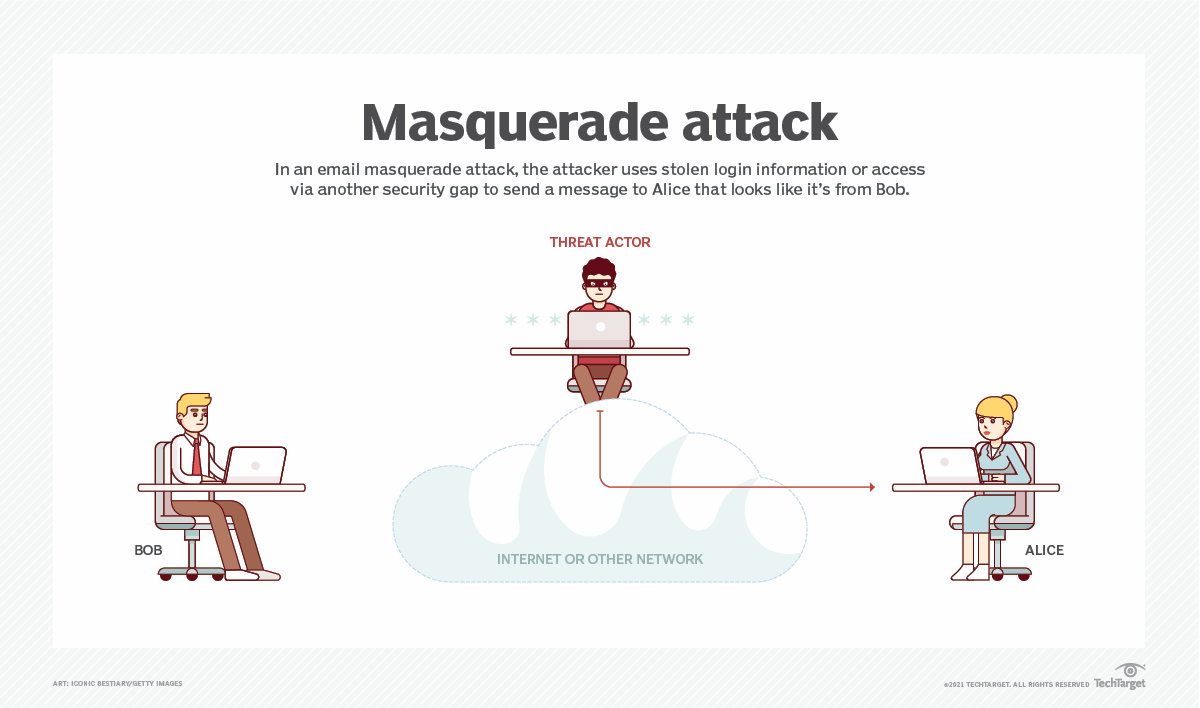
- Masquerading - Masquerading is a type of attack that involves the use of a fake IP address to hide the true identity of the attacker.
- Eavesdropping - Eavesdropping is the act of listening to a conversation without the knowledge of the participants.
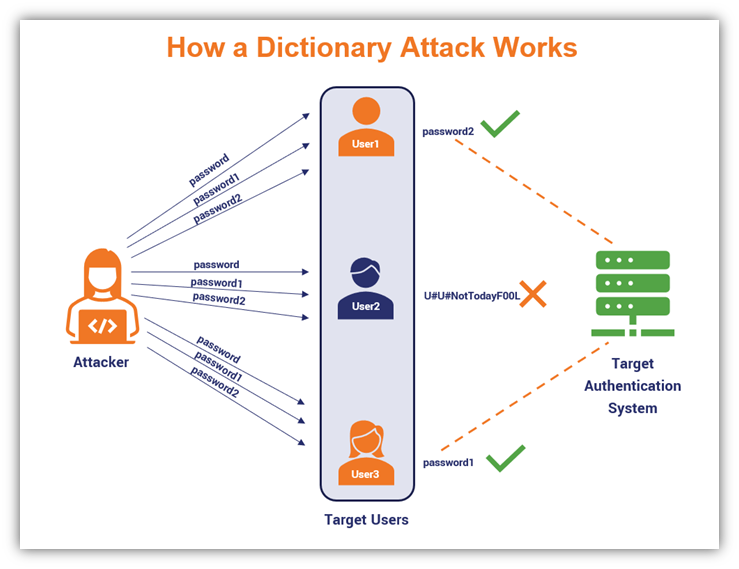
- Dictionary attack - Dictionary attack is a type of brute force attack that uses a list of words to guess passwords.
- Brute force attack - Brute force attack is a type of attack that uses a trial-and-error method to guess passwords.
Active attack
- Guessing - An attack in which an attacker performs repeated logon trials by guessing possible values of the authenticator output.
- Shoulder surfing - A shoulder surfing attack describes a situation where the attacker can physically view the device screen and keypad to obtain personal information.
- Social engineering - Social engineering is the art of manipulating people so they give up confidential or personal information.
Social Engineering , MITM
Define the terms social engineering, man in the middle attack.
Answer
Social engineering: It is psychological manipulation of persons ultimately gaining their trust to reveal confidential information about the organization or the system. There are different types of social engineering techniques used to lure a victim to reveal secret ation. Hackers use o less ood nature to make this kind of access into organization. Pretexting, vishing, tailgating etc. are the normally used as social engineering methods.
Man-in-the middle attack: Attacker acts in between server and client connection. He splits the TCP connection into two and acts as server to the client and a client to the server. Any message is intercepted by the attacker and he is able to manipulate both client and server in his own way.
Eavesdropping & Hybrid attack
What is eavesdropping and hybrid attack?
Answer
-
Eavesdropping: It is snooping into conversation of unsuspecting parties over telephone lines, instant messages, Wireless LANs, etc. Attacker use tools like Air snort, Ethereal and sniff around in any forms of communication that is considered to be private. This includes capturing of network packet in the communication medium.
-
Hybrid attack: It is a password attack which combines the flavor of dictionary attack and brute force attack.
Advance Introduction
Cybercrime , Attacks , Hacking
a) Define Cybercrime? Discuss about various types of Cybercrime.
b) Discuss about email spoofing and email spamming.
c) What is Reconnaissance in the world of Hacking?
d) What is Salami Attack?
Answer
a) 1st Part: Identity theft is a form of stealing someone's personal information and pretending to be that person in order to obtain financial resources or other benefits in that person's name without their consent. Identity theft is considered a cyber crime.
2nd Part: When any crime is committed over the Internet it is referred to as a cyber crime. There are many types of cyber crimes and the most common ones are explained below: Hacking: This is a type of crime wherein a person's computer is broken into so that his personal or sensitive information can be accessed. In the United States, hacking is classified as a felony and punishable as such. This is different from ethical hacking, which many organizations use to check their Internet security protection. In hacking, the criminal uses a variety of software to enter a person's computer and the person may not be aware that his computer is being accessed from a remote location. Theft: This crime occurs when a person violates copyrights and downloads music, movies, games and software. There are even peer sharing websites which encourage software piracy and many of these websites are now being targeted by the FBI. Today, the justice system is addressing this cyber crime and there are laws that prevent people from illegal downloading.
-
Hacking: This is a type of crime wherein a person s computer is broken into so that his personal or sensitive information can be accessed. In the United States, hacking is classified as a felony and punishable as such. This is different from ethical hacking, which many organizations use to check their Internet security protection. In hacking, the criminal uses a variety of software to enter a person's computer and the person may not be aware that his computer is being accessed from a remote location.
-
Theft: This crime occurs when a person violates copyrights and downloads music, movies, games and software. There are even peer sharing websites which encourage software piracy and many of these websites are now being targeted by the FBI. Today, the justice system is addressing this cyber crime and there are laws that prevent people from illegal downloading.
-
Cyber Stalking: This is a kind online harassment wherein the victim is subjected to a barrage of online messages and emails. Typically, these stalkers know their victims and instead of resorting to offline stalking, they use the Internet to stalk. However, if they notice that cyber stalking is not having the desired effect, they begin offline stalking along with cyber stalking to make the victims' lives more miserable.
-
Identity Theft: This has become a major problem with people using the Internet for cash transactions and banking services. In this cyber crime, a criminal accesses data about a person's bank account, credit cards, Social Security, debit card and other sensitive information to siphon money or to buy things online in the victim's name. It can result in major financial losses for the victim and even spoil the victim's credit history.
-
Malicious Software: These are Internet-based software or programs that are used to disrupt a network. The software is used to gain access to a system to steal sensitive information or data or causing damage to software present in the system.
-
Child soliciting and Abuse: This is also a type of cyber crime wherein criminals solicit minors via chat rooms for the purpose of child pornography. The FBI has been spending a lot of time monitoring chat rooms frequented by children with the hopes of reducing and preventing child abuse and soliciting.
b)
-
Email spamming refers to sending email to thousands and thousands of users — similar to a chain letter. Spamming is often done deliberately to use network resources. Email spamming may be combined with email spoofing, so that it is very difficult to determine the actual originating email address of the sender. Some email systems, including our Microsoft Exchange, have the ability to block incoming mail from a specific address. However, because these individuals change their email addresses frequently, it is difficult to prevent some spam from reaching your email inbox.
-
Email spoofing refers to email that appears to have originated from one source when it was actually sent from another source. Individuals, who are sending "junk" email or "spam", typically want the email to appear to be from an email address that may not exist. This way the email cannot be traced back to the originator.
c) Reconnaissance is considered the first pre-attack phase and is a systematic attempt to locate, gather, identify, and record information about the target. The hacker seeks to find out as much information as possible abQut the victim. This first step is considered a passive information gathering. As an example, many have probably seen a detective movie in which the policeman waits outside a suspect's house all night and then follows him from a distance when he leaves in the car. That's reconnaissance; it is passive in nature, and, if done correctly, the victim never even knows it is occurring.
d) Salami attack: A salami attack is a collection of small attacks that result in a larger attack when combined. For example, if an attacker has a collection of stolen credit card numbers, the attacker could 'withdraw small amounts of money from each credit card (possibly unnoticed by the credit card holders). Although each withdrawal is small, the combination of the multiple withdrawals results in a significant sum for the attacker.
Intrusion, Forgery & Attacks
Short note on the following:'
a) Computer Network Intrusion
b) Forgery
c) Passive attack vs. Active attack
Answer
a) Computer Network Intrusion: A network intrusion is any unauthorized activity on a computer network. Detecting an intrusion depends on the defenders having a clear understanding of how attacks work, In most cases, such unwanted activity absorbs network resources intended for other uses, and nearly always threatens the security of the network and/or its data. properly designing and deploying a network intrusion detection system will help block the intruders. As a first step of defence, here's a brief rundown of popular attack vectors.
-
Asymmetric Routing In this method, the attacker attempts to utilize more than one route to the targeted network device. The idea is to have thc overall attack evade detection by having a significant portion of the offending packets bypass certain network segments and their network intrusion sensors. Networks that are not set up for asymmetric routing are impervious to this attack methodology.
-
Buffer Overflow Attacks This approach attempts to overwrite specific sections of computer memory within a network, replacing normal data in those memory locations with a set of commands that will later be executed as part of the attack. In most cases, the goal is to initiate a denial of service (DOS) situation, or to set up a channel through which the attacker can gain remote access to the network. Accomplishing such attacks is more difficult when network designers keep buffer sizes relatively small, and/or install boundary-checking logic that identifies executable code or lengthy URL strings before it can be written to the buffer.
-
Gateway Interface Scripts The Common Gateway Interface (CGI) is routinely used in networks to support interaction between servers and clients on the Web. But it also provides easy openings— such as "backtracking"—through which attackers can access supposedly secure network system files. When systems fail to include input verification or check for backtrack or the pipe characters, a covert CGI script can easily add the directory label " " character to any file path name and thereby access files that should not be available via the Web.
-
Protocol-Specific Attacks When performing network activities, devices obey specific rules and procedures. These protocols—such as ARP, IP, TCP, UDP, ICMP, and various application protocols—may inadvertently leave openings for network intrusions via protocol impersonation ("spoofing") or malformed protocol messages. For example, Address Resolution Protocol (ARP) does not perform authentication on messages, allowing attackers to execute "man- in-the-middle" attacks. Protocol-specific attacks can easily compromise or even crash targeted devices on a network.
-
Traffic Flooding An ingenious method of network intrusion simply targets network intrusion detection systems by creating traffic loads too heavy for the system to adequately screen. In the resulting congested and chaotic network environment, attackers can sometimes execute an undetected attack and even trigger an undetected "fail-open" condition.
-
Trojans These programs present themselves as benign and do not replicate like a virus or a worm. Instead, they instigate DoS attacks, erase stored data, or open channels to permit system control by outside attackers. Trojans can be introduced into a network from unsuspected online archives and file repositories, most particularly including peer-to-peer file exchanges.
-
Worms A common form of standalone computer virus, worms are any computer code intended to replicate itself without altering authorized program files. Worms often spread through email attachments or the Internet Relay Chat (IRC) protocol. Undetected worms eventually consume so many network resources, such as processor cycles or bandwidth that authorized activity is simply squeezed out. Some worms actively seek out confidential information—such as files containing the word "finance" or communicate such data to attackers lying in wait outside the network.
b) Forgery: Offences of computer forgery and counterfeiting have become rampant as it is very easy to counterfeit a document like birth certificate and use the same to perpetuate any crime. The authenticity of electronic documents hence needs to be safeguarded by making forgery with the help of computers abs explicit offence punishable by law. When a perpetrator alters documents stored in computerized form, the crime committed may be forgery. In this instance, computer systems are the target of criminal activity. Computers, however, can also be used as instruments with which to commit forgery. A new generation of fraudulent alteration or counterfeiting emerged when computerized color laser copiers became available. These copiers are capable of high-resolution copying, modification of documents, and even the creation of false documents without benefit of an original, and they produce documents whose quality is indistinguishable from that of authentic documents except by an expert. These schemes take very little computer knowledge to perpetrate. Counterfeit checks, invoices and stationery can be produced using scanners, color printers, and graphics software. Such forgeries are difficult to detect for the untrained eye. It is relatively easy to scan a logo into a completer system and go from there.
c) Passive attack vs. Active attack: Active attacks alter the system or network operations while passive attack gathers information about the system without altering the system. Active attack can involve infecting the system with virus or worms or can span upto deleting the entire hard drive. Normally passive attacks remain undetected. Active attack can flood the entire network with unnecessary packets and can render it slow while passive attack can sniff network packets without changing them. Passive attackers can know the presence of certain user accounts along with their password while active attackers use this information to render the system useless to the owner.
Criminals , CloudComputing
a) Who are cyber criminals? Discuss about various types of Cybercrime.
b) Discuss the role of Cloud computing in cyber security.
Answer
a) 1st Part: A cybercriminal is an individual who commits cybercrimes, where he/she makes use of the computer either as a tool or as a target or as both.
Cybercriminals use computers in three broad ways:
-
Select computer as their target: These criminals attack other people's computers to perform malicious activities, such as spreading viruses, data theft, identity theft etc.
-
Uses computer as their weapon: They use the computer to carry out "conventional crime", such as spam, fraud, illegal gambling, etc.
-
Uses computer as their accessory: They use the save stolen or illegal data.
2nd Part: When any crime is committed over the Internet it is referred to as a cyber crime. There are many types of cyber crimes and the most common ones are explained below: Hacking: This is a type of crime wherein a person's computer is broken into so that his personal or sensitive information can be accessed. In the United States, hacking is classified as a felony and punishable as such. This is different from ethical hacking, which many organizations use to check their Internet security protection. In hacking, the criminal uses a variety of software to enter a person's computer and the person may not be aware that his computer is being accessed from a remote location. Theft: This crime occurs when a person violates copyrights and downloads music, movies, games and software. There are even peer sharing websites which encourage software piracy and many of these websites are now being targeted by the FBI. Today, the justice system is addressing this cyber crime and there are laws that prevent people from illegal downloading.
-
Hacking: This is a type of crime wherein a person s computer is broken into so that his personal or sensitive information can be accessed. In the United States, hacking is classified as a felony and punishable as such. This is different from ethical hacking, which many organizations use to check their Internet security protection. In hacking, the criminal uses a variety of software to enter a person's computer and the person may not be aware that his computer is being accessed from a remote location.
-
Theft: This crime occurs when a person violates copyrights and downloads music, movies, games and software. There are even peer sharing websites which encourage software piracy and many of these websites are now being targeted by the FBI. Today, the justice system is addressing this cyber crime and there are laws that prevent people from illegal downloading.
-
Cyber Stalking: This is a kind online harassment wherein the victim is subjected to a barrage of online messages and emails. Typically, these stalkers know their victims and instead of resorting to offline stalking, they use the Internet to stalk. However, if they notice that cyber stalking is not having the desired effect, they begin offline stalking along with cyber stalking to make the victims' lives more miserable.
-
Identity Theft: This has become a major problem with people using the Internet for cash transactions and banking services. In this cyber crime, a criminal accesses data about a person's bank account, credit cards, Social Security, debit card and other sensitive information to siphon money or to buy things online in the victim's name. It can result in major financial losses for the victim and even spoil the victim's credit history.
-
Malicious Software: These are Internet-based software or programs that are used to disrupt a network. The software is used to gain access to a system to steal sensitive information or data or causing damage to software present in the system.
-
Child soliciting and Abuse: This is also a type of cyber crime wherein criminals solicit minors via chat rooms for the purpose of child pornography. The FBI has been spending a lot of time monitoring chat rooms frequented by children with the hopes of reducing and preventing child abuse and soliciting.
b) Cloud computing and cyber security are the two advanced sectors in IT world making huge changes of working pattern in the field. When these two merge it opens a wide range of possibilities. The cloud computing security provides companies with the availability, reliability, and security they need to conduct business in a global marketplace. Advanced cyber security features combine with physical infrastructure to create a comprehensive, secure solution to your cloud computing needs. As companies migrate more and more of their data and infrastructure to the cloud, the question of cloud computing security becomes paramount. Cloud security provides multiple levels of control in a network infrastructure to afford continuity and protection. It's an essential ingredient in creating an environment that works for companies around the world. The benefits of cloud computing can be affordably attained by partnering with advanced private cloud computing providers in a way that doesn't jeopardize your company's security. At a time when cyber attacks are growing worldwide, and high-profile cybercrime such as data theft, ransomware and computer hacks have become the order of the day, experts believe that cloud computing may provide the security against cyber threats that companies need. They reason that Cloud helps security operations respond quicker to threats and focus on business risk as opposed to spending countless hours researching threats and trouble-shooting aging on-premises systems. It also saves a substantial cost for organizations in the long run.
Social Networking
"Social Networking is increasingly becoming a source Of cybercrime." Explain.
Answer
As social networking becomes more a part of our daily lives, individuals find this technology an attractive vehicle to perpetrate cyber crimes. Anonymity provided via social networks allows a person to easily portray another user's identity. Cyber criminals exploit such vulnerabilities to steal user credentials, which in turn can be used to breach a company's network infrastructure. The term cyber crime is confirmed as the official crime term as criminals started getting more aggressive over the online and becoming a threat for millions of Internet users. Identity theft is the key threat to many social media users, as millions of online users use their personal information in order to getting registered with one or more social media platforms. Such huge information with personal data of so many people is one of the easiest targets for many cyber criminals. Many users also use their credit or debit card to purchase different products, items or services through these social networking sites. This is why the cyber criminals around the world continuously try to get inside the personal details of many users from those social media platforms. We can minimize the threat of cyber attack or cyber crime by getting a little aware and conscious while using social networking sites.
Software Piracy
What are the different types of software piracy? What are the risks involved in using pirated software?
Answer
1st Part:
According to some people "Software piracy is copying and use of Software without proper license from the developer. Similarly, simultaneous use of single user license software by multiple users or loading of a single user license software at multiple sites, also amounts to software piracy. Using trial version software for commercial gains is also piracy, Piracy is also can be punishable if you install an pirated software do your work and then delete this software from the machine with enough evidences to show the activity. Any Copyright infringement is the unauthorized use of copyrighted material in a manner that violates one of thc copyright owner's exclusive rights, such as, the right to reproduce or to make derivative works that build upon it. For electronic and audio-visual media, such unauthorized reproduction and distribution Of a copyrighted work is often referred to as piracy (however there is no legal basis for the term 'piracy' There are different types of software piracy such as copying of copyrighted materials and using multiple copies of the same without license. Even if a person installs and uses the copy of the material and then removes it from the system, it will also be reported as software piracy. It includes installation on hard drive or on servers and clients with same version and no license. Ifa company illegally sells the product of another company without their permission or authorization with or without alteration of the original product can be considered as piracy,
2nd Part:
Apart from getting caught and termed a three years of imprisonment, an offender can be charged with fine of Rs 50,000 to Rs 2 lakhs or both. The software can be corrupted or can be of low or degraded quality. The software can contain malware's or Trojans that can cause data theft or may lead to disabled system or infected network. Pirated software can cause reputation loss in a business and can end contracts with the clients.